


Computer Architecture for Brain-Computer Interfaces
Earlier this year, Elon Musk’s Neuralink demonstrated an implantable brain-computer interface (BCI) capable of recording electrophysiological activity from several thousands of biological neurons with high fidelity and signal resolution. Such implantable BCIs offer...
Building Fault-Tolerant Qubits Using More Physical States
Continuing with our thread on looking past abstractions in quantum computing, guest bloggers Yunong Shi from EPiQC and Christopher Chamberland and Andrew Cross from IBM examine how to make qubits fault tolerant by exploiting more of the physical state space available...
RE-gem5: Building Sustainable Research Infrastructure
RE-gem5 is a directed effort to rejuvenate the underlying infrastructure of gem5. RE-gem5 is not a new simulator or a new project; it is a project to enhance and support the current gem5 infrastructure. The community-developed gem5 infrastructure is one of the most...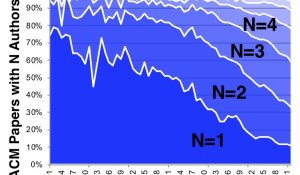
Scaling the Field: Collaboration is of the Essence
Graduate student growth continues to outpace faculty growth in computer science. Because producing successful graduate students requires publishing with them, each faculty member should be publishing more, but they are not. If research quality has dropped over time, as some perceive, the reason in not an increase in per-author output.

Accelerator-Level Parallelism (ALP)
The demand for computing performance continues to grow exponentially in part due to video and machine learning processing for applications like augmented/virtual reality and self-driving vehicles. However, the underlying advances (Moore’s Law and Dennard...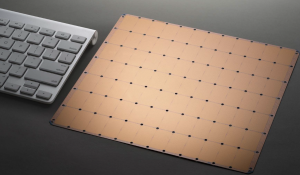
The First Trillion-Transistor Chip: A New Design Space
There was stunning news at the HotChips-31 conference held at Stanford Memorial Auditorium last week. Cerebras, a startup company working on machine learning accelerators in stealth mode, finally came out and presented a groundbreaking accelerator chip packed with 1.2...
CARES First Birthday Blog
CARES seeks to advance the strength and impact of our community’s research, by helping to build a stronger and more supportive research community.

Deep Neural Network Acceleration Beyond Chips
This week Cerebras announced a bold design to accelerate deep neural networks with silicon that is not cut into chips. AI and Moore’s Law: Artificial Intelligence (AI) is much in the news for what it can do today and the promise of what it can do tomorrow (CCC/AAAI...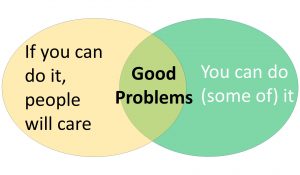
Increasing Your Research Impact
Many works present their results; this blog post seeks to aid you in developing your own great results, especially in computer architecture and systems. I learned these lessons over a career leading to an Eckert-Mauchly Award. I structure this blog post with steps of the scientific method.

