
by Toru Koizumi, Ryota Shioya, Hidetsugu Irie on Apr 2, 2025 | Tags: Architecture, CPU, gpu, ISA Design
CPU cores have become significantly wider over the past decade. Ten years ago, the highest-performance CPUs could decode only up to four instructions simultaneously and execute up to eight instructions. However, top-tier CPUs released in recent years have grown to...
Read more...
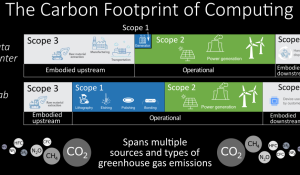
by Daniel S. Berger, David Brooks, Fiodar Kazhamiaka, Mark D. Hill, Ricardo Bianchini, Carole-Jean Wu, Karin Strauss, Kali Frost, Jaylen Wang, Kevin Martins, Sharon Gillett, Esha Choukse, Dan Ernst, Rodrigo Fonseca, Kari Lio, Bhargavi Narayanasetty, Pratyush Patel, Celine Irvene, Akshitha Sriraman, George Porter, Alex Jones, Udit Gupta, Bilge Acun-Uyan, Kim Hazelwood, and Doug Carmean on Aug 3, 2023 | Tags: Accelerators, amd, apple, Architecture, Carbon emissions, Cloud computing, Datacenters, embodied carbon, intel, Measurements, nvidia, operational carbon, qualcomm, Sustainability, tsmc
A recent post raises awareness of the challenges of reducing operational carbon, while also controversially challenging the importance of embodied carbon. We rebut the arguments raised against using embodied carbon as a design metric and conclude by advocating for more research on reducing embodied carbon.
Read more...

by Sudhanva Gurumurthi, Vilas Sridharan, and Sankar Gurumurthy on Jul 17, 2023 | Tags: Architecture, Debugging, fault tolerance, faults
Overview Reliability is essential for computing. However, as technology nodes have scaled, there have been several fundamental physical challenges to overcome to provide the abstraction of reliability. One such challenge has been the emergence of marginal...
Read more...

by Hyeran Jeon, Dong Li, Jie Ren on May 31, 2023 | Tags: Architecture, Conference, CXL, Heterogeneous and Composable Memory, hpca, Memory
Introduction Memory systems are evolving into heterogeneous and composable architectures. Heterogeneous and Composable Memory (HCM) offers a feasible solution for terabyte- or petabyte-scale systems, addressing the performance and efficiency demands of emerging...
Read more...
by Richard L. Sites on Dec 19, 2022 | Tags: Architecture, Data Centers, Memory, Performance
When I worked at Google, fleet-wide profiling revealed that 25-35% of all CPU time was spent just moving bytes around: memcpy, strcmp, copying between user and kernel buffers in network and disk I/O, hidden copy-on-write in soft page faults, checksumming, compressing,...
Read more...






